


Bring Your Own Device (BYOD) is a business concept in which employees can use their own devices for working-related tasks. BYOD can be a solution for smartphones, laptops and tablets. BYOD laptops and tablets are typically associated with freelance staff, fulfilling a temporary role in the organization. BYOD for smartphones is more widespread since this is not just a solution for freelancers. Many organizations allow their staff to use their personal smartphones for business-related tasks. BYOD has some attractive benefits, but it also brings some serious security challenges. We will address them in this article.
Free Trial: Auto-Login for Desk Phones
In general, BYOD offers many benefits for both employees and employers:
Still, the BYOD model also brings some serious security challenges. The main concern for many organizations is the risk of unauthorized access to sensitive company and client data. This is usually manageable for laptops since most business laptops will meet the bare OS and security requirements, and the virtualization office separates business data from personal use and data. Tablets and smartphones, with many different device types and OS versions, are more complicated to secure. Personal devices may lack the robust security features of corporate-managed devices and, therefore, are more vulnerable to malware, data breaches, and other cyber threats.
Solutions like containerization (separating business and personal data and apps), Mobile Device Management (MDM), Mobile Applications Management (MAM), remote wipes and Data Loss Prevention (DLP) certainly will help manage and secure BYOD devices. Still, these are complex and costly solutions.
Specifically for staff working mainly at a computer, one may argue whether a BYOD smartphone is always necessary. Every app is easy – and often simpler – available via someone’s computer or laptop. What remains is someone’s accessibility. The office’s desktop telephone typically still offers the best conversation quality. However, in modern flex-office buildings, you always want to be reachable via your own number. You also want to use your own contacts, features and settings.
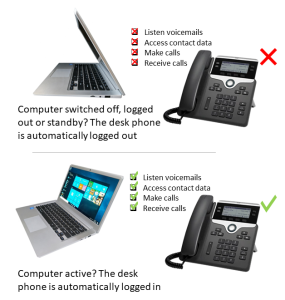
That is what we can solve for you. With the combination of Cisco Extension Mobility + RSconnect ALM feature, you can log automatically into any telephone without typing a username and PIN. And if working from home, you can rely on the Cisco Jabber software and the RSconnect Forwarding Assistant.
In short, looking for a alternative for smarphones? Check our options